Conspiracy Theory Confirmed: Researcher Shows How Phone Shows Ads Based on Conversations It Hears
 By John Vibes
By John Vibes
For years, smartphone users have been growing increasingly suspicious that their devices are listening to them to feed them advertisements and to “enhance their experience” on third-party apps. Companies like Google and Facebook have consistently denied these claims, saying that targeted ads and messages are merely a coincidence, and that data for these services are taken in other ways.
However, earlier this year during the Cambridge Analytica scandal we began to see some of the first hints that our phones may actually be listening to us.
Cambridge Analytica whistleblower Christopher Wylie says that they have probably been listening all along. During an appearance before the UK parliament, Wylie said, “There’s audio that could be useful just in terms of, are you in an office environment, are you outside, are you watching TV, what are you doing right now?”
Since the scandal, experts who have studied this possibility began revealing their surprising results.
In a recent interview with VICE, Dr. Peter Hannay, the senior security consultant for the cybersecurity firm Asterisk, explained how third-party apps exploit a loophole to gather the voice data from your phone.
Hannay said that while your microphone is always on, your voice data is only sent out to other parties if you say specific trigger words such as “Hey Siri” or “OK Google,” but there is a catch. Third-party apps often ask to gain access to voice data in their user agreements to “enhance the experience” of their products.
“From time to time, snippets of audio do go back to [other apps like Facebook’s] servers but there’s no official understanding what the triggers for that are. Whether it’s timing or location-based or usage of certain functions, [apps] are certainly pulling those microphone permissions and using those periodically. All the internals of the applications send this data in encrypted form, so it’s very difficult to define the exact trigger,” Hannay said.
While this process is becoming more obvious by the day, many tech companies continue to deny that they are engaged with this practice, and since all of the outgoing information is encrypted there is no way of telling exactly which information they are getting and how they are using it.
“Seeing Google are open about it, I would personally assume the other companies are doing the same. Really, there’s no reason they wouldn’t be. It makes good sense from a marketing standpoint, and their end-user agreements and the law both allow it, so I would assume they’re doing it, but there’s no way to be sure,” Hannay said.
VICE reporters then conducted their own experiment, saying random phrases into their phones and then seeing advertisements affiliated with those terms pop up in their news feeds. You can try this experiment at home yourself, and it is highly likely that you have experienced results like this by accident.
In April, I experienced something like this when a friend visited my house from the West Coast. I picked him up from the Baltimore-Washington airport and during a conversation about his flight, he told me that he had a layover in Charlotte, North Carolina, and mentioned that they had a nice airport.
The following morning I woke up with these messages on my phone:
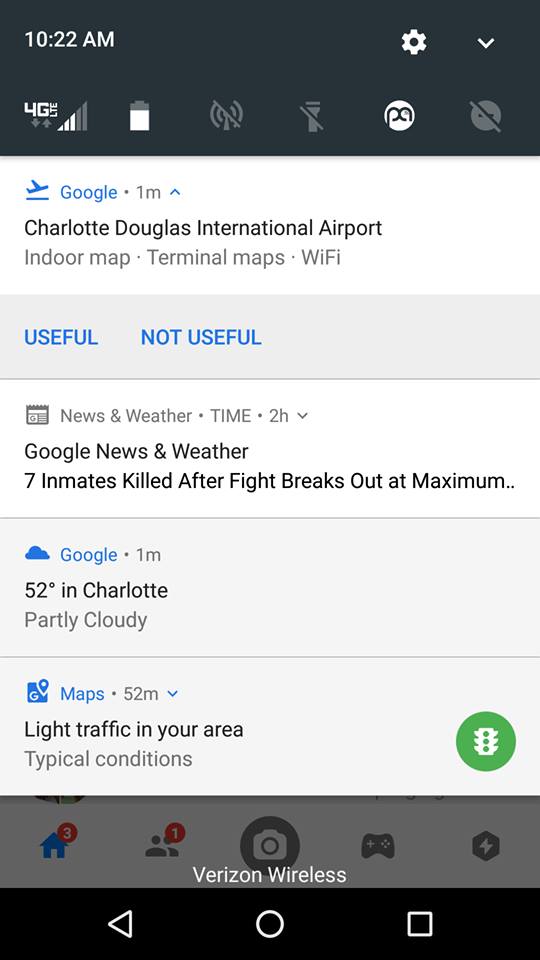 Oddly enough, I have never been to Charlotte, North Carolina, never really thought about the place, and have never typed anything about that place into Google or Facebook. But, sure enough, after having a conversation about the airport in Charlotte, my phone thought I was interested.
Oddly enough, I have never been to Charlotte, North Carolina, never really thought about the place, and have never typed anything about that place into Google or Facebook. But, sure enough, after having a conversation about the airport in Charlotte, my phone thought I was interested.
As of right now, there is no way to avoid this spying, aside from being extremely careful about the apps that you sign up for, and actually reading their user agreements—or getting rid of your cell phone altogether, which could be counterproductive if you use it for business.
John Vibes is an author and researcher who organizes a number of large events including the Free Your Mind Conference. He also has a publishing company where he offers a censorship free platform for both fiction and non-fiction writers. You can contact him and stay connected to his work at his Facebook page.John just won a 3-year-long battle with cancer, and will be working to help others through his experience, if you wish to contribute to his treatments consider subscribing to his podcast to support . This article first appeared at The Free Thought Project.








